One of the most problematic port redirections are those redirecting UDP ports. Based on SSH protocol, there is no way to redirect UDP ports over SSH tunnels. Imagine you are behind a FW with very restrictive rules and your connection must use a Proxy witn no name resolutions outside of the intranet, there are no too much ways to access to an external DNS and surf internet, but there are some…
Here it is explained a way how to redirect UDP ports with the help of socat (NetCat+++), and a SSH tunnel.
To do that you will need some things, like a putty client, a remote server where to connect over SSH, SSH tunnels, port redirections, a remote DNS server, and socat (window version and linux version).
Netcat can be downloaded from:
http://www.dest-unreach.org/socat
Our linux external SSH server must have next parameter set in /etc/ssh/sshd_config
AllowTcpForwarding yes
Let’s begin configuring the PuTTY to be able to connect remotely.
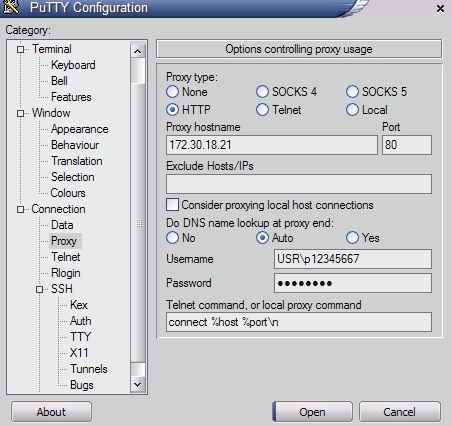
Configure you PuTTY with proxy details like in this capture:
In remote address, you will configure your remote SSH server like sshserver.myserver.com.
Note*: Usually, firewalls block external connections to SSH ports (22), but threre is a trick using port 443 as SSH port in your SSH server configuration (Listen 443). As the communication is encrypted, all the firewalls I know, allow any encrypted connection to remote 443 ports (like it would be a HTTPS connections) but in this case, is our SSH server ;).
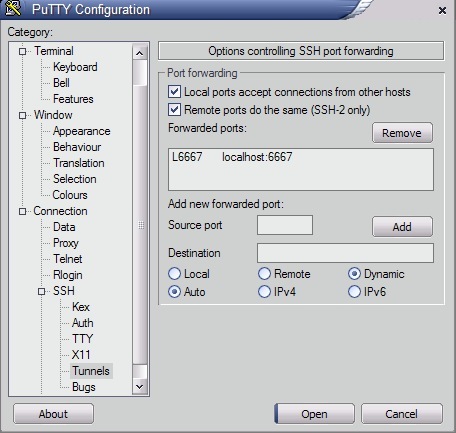
After this, configure a some tunnels, in tunnels PuTTY options like this one:
open the communication and do login in your remote server.
In the remote server run socat and listen in the 6667 port redirected with PuTTY.
sshserver:/usr/bin/socat-2.0.0-b3# ./socat -v -d -d -s -T 1 tcp4-listen:6667,reuseaddr,fork UDP4:192.168.1.1:53
where 192.168.1.1 is our DNS server and tcp4-listen:6667 is the port tunneled.
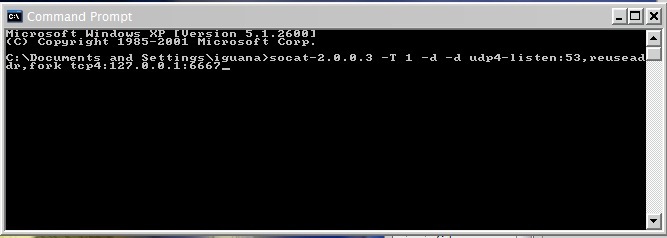
Now locally in the windows machine, run socat with next parameters:
C:\> socat-2.0.0.3 -T 1 -d -d udp4-listen:53,reuseaddr,fork tcp4:127.0.0.1:6667
like this capture:
Last step is add 127.0.0.1 as our primary DNS server in windows.
Now remote servers will be resolved using this just-a-little-bit-complicated way ;-)
I know, it is not easy, usefull only in specific cases and you need a lot of things to make it work, but it is funny!!! :)